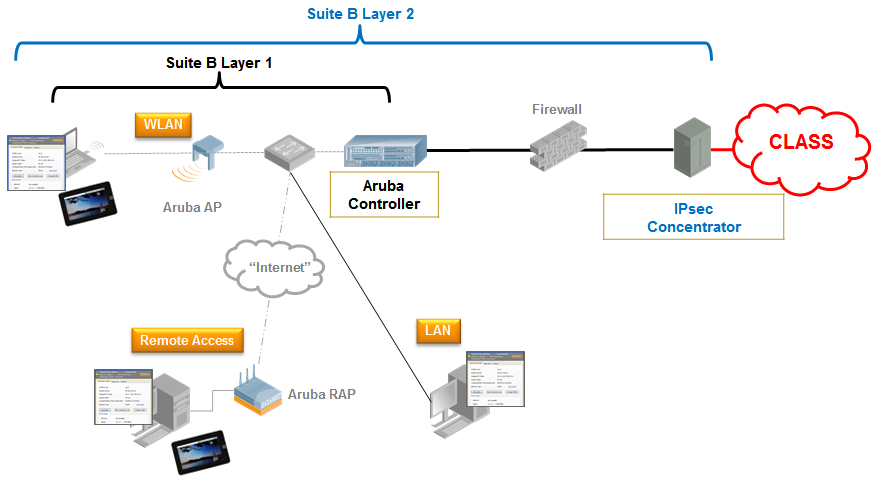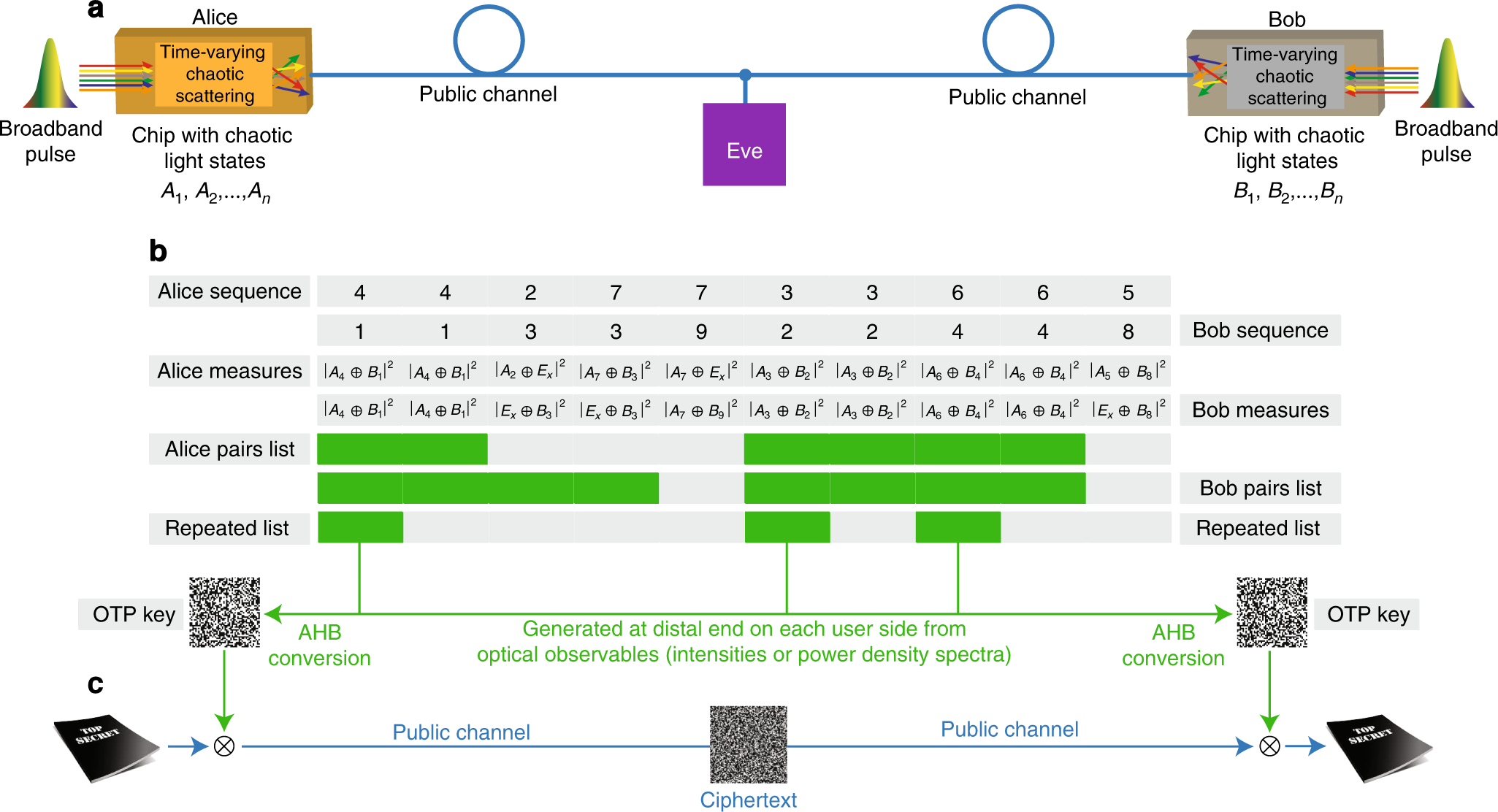
Perfect secrecy cryptography via mixing of chaotic waves in irreversible time-varying silicon chips | Nature Communications

A. Steffen, CryptoStrength.pptx 1 Information Security 2 (InfSi2) Prof. Dr. Andreas Steffen Institute for Internet Technologies and Applications. - ppt download
GitHub - westerndigitalcorporation/sweet-b: Sweet B is a safe, compact, embeddable library for elliptic curve cryptography.





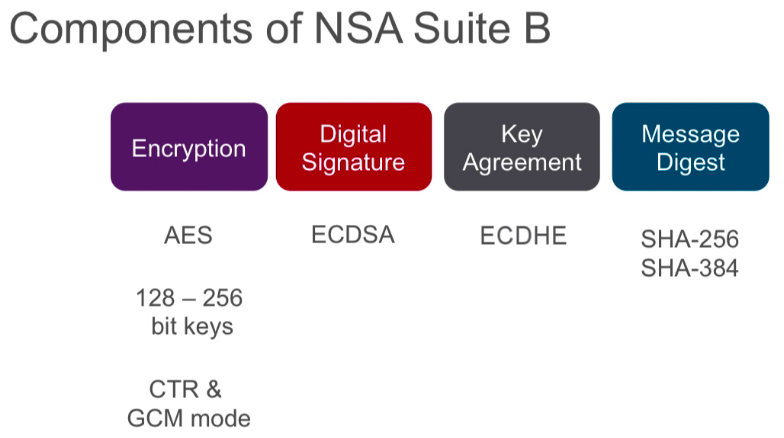


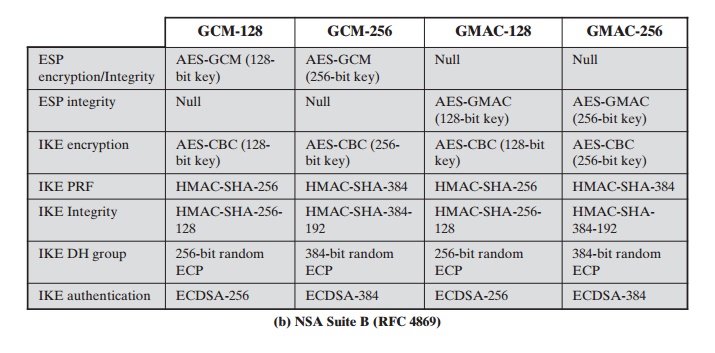




![PDF] Suite B Cryptographic Suites for Secure Shell (SSH) | Semantic Scholar PDF] Suite B Cryptographic Suites for Secure Shell (SSH) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d27872cc52341adf392c2295a45daf06688b5cb2/5-Table1-1.png)